Is RF Technology the Answer to Fraud?
The massive data breach at Target had one beneficial effect: It opened people's eyes to the fact that even the most robust security system can be hacked. By all accounts Target's is a model, multi-tiered system whose defenses are in excess of what is required by Visa and Mastercard's already tough safeguards. But the hackers got in anyway, which immediately led to an outcry over why credit card transactions in the U.S. are not more secure, and a call for the use of contactless cards that require no physical "swipe" through a reader. Thanks to this outcry, Visa, MasterCard, and American Express have been firm: Retailers must invest in smart card-capable readers by October 2015. For those who do not, the responsibility for fraud losses will become totally theirs.
After all, smart cards (cards with embedded ICs that contain encrypted information and secure processing capability- but still require contact) have been used throughout the developed world since 1983 and have dramatically reduced theft. It took so long to get to this point in the U.S. because even though fraud cost retailers and banks more than $12 billion in 2013, it was still apparently less expensive when weighed against the cost and complexity of updating retail point-of-sale (POS) systems. But the Target breach has opened Pandora's box, and even though the cards themselves were not a vehicle for the Target attack and the information obtained was probably encrypted using a 128-bit cipher (and thus useless to the hackers), momentum for employing advanced payment techniques is probably unstoppable at this point.
However, even a massive step forward to widespread smart card use won't bring the retail industry into the 21st Century, as technology has moved on. The standard today is contactless smart cards that employ wireless communications and require no physical "swipe" between card and reader, and smartphone-based Near Field Communications (NFC) technology that eliminates the need for a card altogether. However, rarely mentioned in the furor over the Target breach is one key fact: The cards themselves weren't the problem.
The Cards Weren't to Blame
The miscreants who perpetrated the Target attack did so by installing malicious software on point-of-sale (POS) terminals at Target stores using "memory-scraping" tools that grab data stored momentarily by terminals during a transaction. However, this malware got to the terminals through a corporate Target Web server that gave the hackers access to company terminals. Once comfortably ensconced in the terminals, it set up its own control server on Target's corporate network, storing all of the stolen data on Target's own data repositories until the hackers got around to offloading it.
Of the reported 40-plus antivirus tools the company uses to scan for malware traversing its network, none either found it or if found, considered it malicious. The software, called BlackPOS, can be purchased for around $2,000 on cybercrime forums and is tailored for bypassing firewalls and installing itself on point-of-sale terminals. So in short, the corporate servers, not the POS terminals, were the point of entry as the thieves came in from the "back end" rather than the POS terminals at the front.
All POS terminals collect data, whether they require you to swipe a card or place it within a few inches of the reader. Thus the question: What makes contactless cards more secure than standard cards and would they make a big difference in credit card theft? In Target's case probably not, but they would certainly be a major improvement over the current system for the majority of more common types of thefts at the terminals themselves, which are much more frequent. To illustrate where the U.S. stands in payment security, let's look at the current viable mag-stripe alternatives--smart cards, contactless cards, and near-field communications, as well as RFID, which is different from all three.
Not So Smart
In a passive RFID system (the most common type), the reader transmits a weak signal that is captured by a loop antenna (Figure 1) on the card, rectified, and the tiny amount of resulting power employed to respond to the reader's query and identify itself. The control system matches the identity code with information in the database for authentication. In this regard RFID and contactless payment have two basic things in common: They use wireless technology to eliminate the need for a physical connection between the POS reading device and the item being read and incorporate an IC and memory for data storage. However, with a few minor exceptions the similarities end there. For example:
- Passive RFID tags are extremely inexpensive (typically less than a dime) and are thus ideally suited for high-volume tracking of virtually anything on which an RFID tag can be placed or inserted. Active RFID tags contain a battery so that they can send bursts of information but are much more expensive and thus much less widely used.
- RFID tags have little or no "intelligence," while both contact and contactless "smart" cards have significant security features including secure microprocessors and memory and cryptographic processing capability.
- RFID tags can be read from a distance of about 6 in. (passive) to more than 650 ft. (active) away from the reader while for security reasons contactless cards can be read from only about 2 inches away.
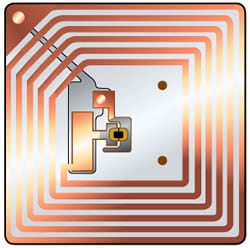
Figure 1: An RFID tag employs a minimum of components, the largest of which is the loop antenna that captures the weak signal from the reader.
RFID has naturally evolved to be used in those applications in which its strengths make it advantageous, even including passports that contain an image of the owner. In 2005, Walmart told its top 100 suppliers to put RFID tags on cases and pallets of goods going to its distribution centers, a program that was later extended to all suppliers. The company has reported that RFID-tagged out-of-stock items can now be replenished more than three times faster than before the program was implemented. The U.S. Department of Defense followed suit as have many other companies and today passive RFID is broadly used throughout many industries.
In short, while RFID systems have become ubiquitous in tracking-type applications, their lack of intelligence and limited ability to provide security have except in a few instances kept them from use in transaction processing.
Smart Cards
The smart card (Figure 2) must be mentioned here because it was the first card designed for transaction processing to overcome the security limitations of "dumb" magstripe cards. A smart card provides significant security features including active encrypted authentication using symmetric DES (Data Encryption Standard), 3DES (triple DES), or public key RSA encryption with keys up to 1024 bits in length.

Figure 2: A generic smart card showing the contacts that access the internal electronics.
Smart cards employ an embedded IC that includes memory and a microprocessor. The device's eight exposed metallic pads provide access for DC power, reprocessing by the POS reader, a clock signal, ground, and serial I/O. The onboard processor, which today is typically a 32-bit RISC processor running it up to 32 MHz, executes instructions and the controller manages data flow to and from the card and reader. The card also contains three types of memory: ROM for permanent instruction storage. RAM for temporary storage, E-PROM for running applications.
Contactless Cards
Contactless cards retain the aforementioned smart card components and security features except for the former's electrical contacts, which are replaced by the RF section that is similar to that used in RFID, and eliminates physical contact with a POS reader. Additional security is provided by the fact that you need not enter a PIN during every transaction but after a certain number of transactions, the card reader will request the PIN to maintain security.
The amount of each transaction is also limited and is presently quite low. Contactless cards were first used for electronic ticketing in Korea in 1995, and many people in the U.S may remember Exxon's Speedpass system fielded in the late 1990s that is still used in many ExxonMobil stations. Contactless technology has since been adopted by MasterCard, Citibank, JPMorgan Chase, American Express, and many other organizations. Current examples include Visa's PayWave, ExpressPay from American Express, and MasterCard's PayPass system.
Near-Field Communications (NFC)
NFC is yet another entry into the wireless "contactless" mix. It is a set of communications protocols and data exchange formats and standards designed for use on smartphones and tablets that is similar to contactless cards - but without the card. NFC was developed under the auspices of the NFC Forum created in 2004 by NXP, Sony, and Nokia. It has been embraced by GSMA, which has defined and is refining an architecture for GSMA NFC standards that are specific to the carrier wireless world.
The technology and standards are evolving. Google has incorporated its Host Card Emulation (HCE) in Android 4.4 (KitKat) but does not follow the GSMA standards. The first smartphones to include PayPass or payWave became available in 2011, and many more have since been added. In February of this year, MasterCard announced a joint venture between EE, Telefónica UK, and Vodafone UK, to advance the technology and make contactless payment a universal platform in Europe.
NFC shares a basic approach with other contactless technologies, including RFID, since it uses magnetic induction between loop antennas. When placed close to each other (that is, in their near field) the antennas create a virtual transformer that generates a voltage. NFC operates in the unlicensed Industrial Scientific and Medical (ISM) band at 13.56 MHz and has a theoretical working distance of 8 inches, but in practice is more like 2 inches or less.
NFC also differs from contactless smart cards in that it allows communications both to and from the reader, and has the benefit of the smartphone's massive processing, security, and encryption capabilities as it is not constrained by a credit card-sized form factor. Google's Android Beam uses NFC to enable Bluetooth on the phone, and allows the point-of-sale reader to pair them while also disabling Bluetooth until a transaction or file transfer has been completed. Another variant called S-Beam used by Samsung in its Galaxy series products, while similar to Android Beam, instead uses NFC to share MAC and IP addresses and employs WiFi Direct to share files and documents. It is considerably faster than Bluetooth, with data rates up to 300 Mb/s, which makes sharing large files much faster.
PayPal has decided to go its own way, abandoning NFC technology altogether and calling it, as president David Marcus noted in a blog last year, a technology that will "fail to gain mass adoption" and "slowly die in 2013," a projection that has thus far proven to be wrong. Instead, PayPal is using Bluetooth Low Energy (BLE) technology in a service called Beacon that was announced last September. Beacon lets customers pay without either a smartphone or a card. Retailers require a $100 USB dongle plugged into their point-of-sale systems (Figure 4), and when a customer whose phone has a Beacon app approaches, he or she will be prompted about whether or not to select PayPal as the payment source.

Figure 3: Paypal's Beacon reader plugged into a wall jack. The $100 device connected to a POS terminal via USB.
The app need not be open on the phone and no signal or GPS location information is required. The app allows customers to optionally store the Beacon-compliant retailers into the phone so that payment is basically hands-free and painless. It leapfrogs the company's current payment system that requires the customer to open the PayPal app on the phone and check with the retailer every time.
NFC is not just useful for payments, but for loyalty programs, transit passes, and other applications. For example, Google's HCE allows any app running on an Android 4.4-enabled device to emulate a smart card, and users can simply open the app and initiate transactions. This opens up virtually limitless possibilities, from social networking to sharing contacts, photos, and large data files or videos, and mobile multiplayer games.
While NFC has gradually been gaining acceptance, its numerous potential uses make it highly appealing, which led AT&T, Verizon, and T-Mobile in 2011 to create a joint venture called "ISIS," with the mission of creating a single architecture on which NFC specifications can be used by their customers to make mobile payments. Its overarching goal is to allow NFC-enabled smartphones and other wireless devices to function like credit cards, potentially cutting contactless cards off at the knees. However, it's much more likely that the two will coexist, as not everyone is comfortable abandoning physical cards and using their phone as an all-inclusive payment device.
Summary
It only makes sense that some form of contactless payment system should replace mag-stripe cards in the U.S. It's just taken forever to arrive. There are definite advantages in security afforded by smart cards, contactless cards, and phone-based NFC that almost certainly will reduce incidences of theft. Nevertheless, as the Target breach has amply demonstrated there is no panacea that will entirely eliminate fraud, as long as there are criminally-minded hackers among us who can completely ignore the POS and simply enter at the corporate level.
And as contactless payment systems become more popular, hackers will certainly turn their attention to finding ways to exploit it as they already do on the Web and in PCs. Even so, consumers will benefit, as will banks, credit card companies, and retailers, once the cost of updating their systems has been amortized over time.